What exactly is Endpoint Detection & Response (EDR)?


What is endpoint detection and response (EDR)?
Many people in IT have a general idea – but don’t know what extent of cybersecurity it provides. I’ve been on many calls regarding EDR, and some of its most important aspects aren’t fully understood. The purpose of this article is do a deep dive into what EDR is, and how it can do the following in order to improve your security posture:
- Automatically protect your end-users through machine-learning and AI
- Proactively threat hunt and remediate
- Reduce the workload of you and your team
- Provide you with forensics and reporting should an attack occur
- Give you peace of mind while it works for you 24/7/365
I like to keep things interesting – so I’ve chosen a movie to correlate what EDR is and how it works. This time around? One of Arnold Schwarzenegger’s greatest films, as well as one of the greatest films of the 80’s: Predator (1987). But first, a quick overview…
Legacy AV vs Modern EDR

First and foremost – it’s important to understand the difference between Legacy AV and Modern EDR. As the chart shows above, we went from signature based detection, to real-time anomaly detection via machine-learning and AI. No longer do we have to wait for malware or viruses to be detected beforehand – we can now proactively stop zero day attacks or other malicious activities that have yet to be discovered.
This is done by setting a baseline of your current environment. Once the platform knows what is normal, it can “learn” when something doesn’t seem right. On top of that, with Ransomware, for instance – if the platform detects a sudden large amount of files being encrypted, it will determine that this is most likely a ransomware attack. While each platform is different, they all have the ability to respond in a way they’re configured to. So, should this anomaly be detected, you can choose to have it alert you and your team, lock down the machine(s), quarantine them, etc.
How exactly does EDR work?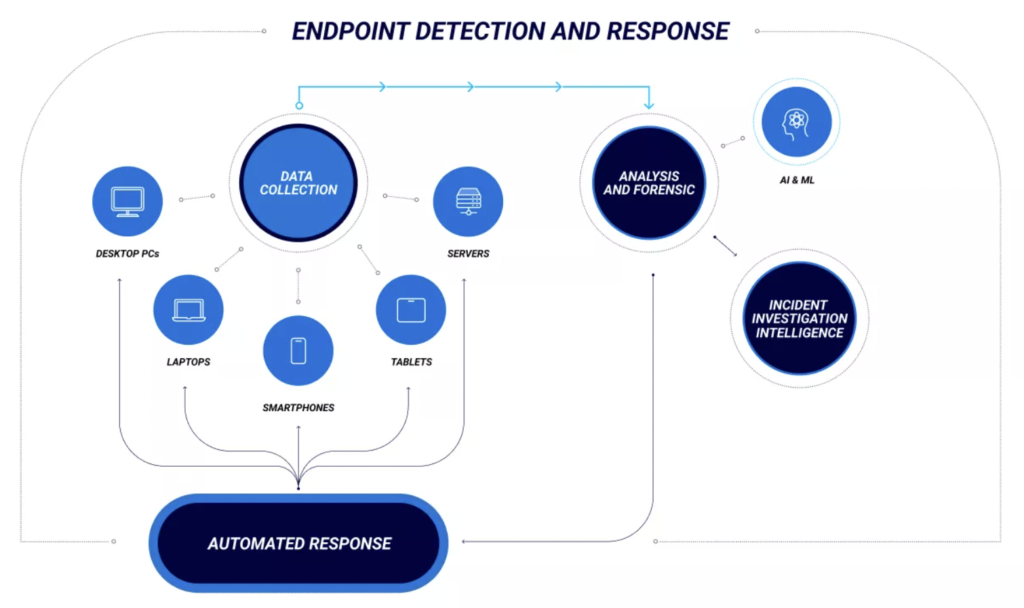
The EDR platform of choice collects data from all endpoints – and from there can make an automated response. On top of that, Analysis and Forensics allow you to visualize how the malicious event occurred and how to prevent it in the future.
Endpoint Detection & Response – Visibility Criticality
In “Predator”, there are several different characters we can compare to an EDR threat situation. First, we’ve got Major Alan “Dutch” Schaefer (Arnold) and his team of mercenaries, who act as the EDR. Their task is to hunt down guerrilla forces (ransomware) who have kidnapped political cabinet members (important PII data). In the process of doing so, Dutch’s group runs into the Predator, a “Zero-day-attack” that nobody has ever seen before. In order to defeat him, they have to adapt their tactics and learn about his weaknesses.
In the real EDR world – it is very similar. One of (if not the) most important aspect of Modern EDR is its Machine-Learning capabilities. Below is the process of how this works in general:

To translate this into the EDR world:
- The platform gathers data from the environment it is protecting. This could be an anomaly it detects – for example a mass amount of files suddenly being encrypted (which would insinuate ransomware).
- Data received is “cleaned”, meaning that duplicate, irrelevant, or incomplete data is removed.
- An algorithm and model are built based on the anomaly that was detected.
- A “prediction” is created through this initial process – the platform has “learned” about the threat, and now can detect it far quicker in the future.